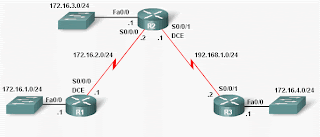
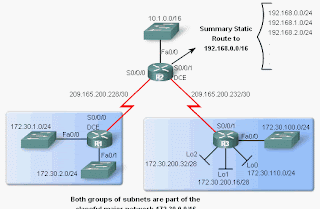
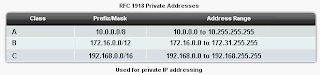
XP Protection Center, despite its deceptive skin, bears no real resemblance to the actual XP Security Center. Even if it was an actual protection program, XP Protection Center just doesn’t act...
like the real thing.
First of all, the XP Security Center only monitors certain security features on your computer. It lets you know that your Firewall, Automatic Updates and Antivirus Program are running and working correctly. Unlike XP Protection Center, it does not tell you whether or not you’re infected.
Actually, XP Protection Center only tells you that you’re infected once it infects you itself. This whole process goes further, far beyond the scope of the real XP Security Center. The real thing is preinstalled on your computer, and you don’t have to pay for updates or upgrades. You may never see it unless you open it in the Control Panel.
With XP Protection Center, however, it pops up once you’re infected. It does a scan, telling you that your temporary files are infected. In reality, your temporary files are almost never infected. They’re only your Internet browsing history.
Then XP Protection Center tells you that you need to buy the upgrade to kill your infection. You would never see this with the real Security Center. Of course, if you buy it, you open up a whole different can of worms.
If you buy the XP Protection Center “upgrade,” you get a junk program for an insane amount of money. Not only that, but you might have more problems with your credit account. It has been known to happen that whoever is running this program can take every cent out of credit accounts. Unfortunately, they can’t be touched by the United States legal system.
You may also notice that the XP Protection Center web page isn’t on the Windows website. If you weren’t suspicious about it before, this should really clue you in. With Windows products, you will only go to the Windows page.
The biggest difference between the XP Protection Center and the real Security Center is that the first is a bundle of spyware, while the second is a monitoring program that’s part of the Windows OS. The scanning pop up is an old spyware trick, as is the browser redirection. These are all delivered by a Trojan Downloader spyware program called Zlob.
Also, you only get the real XP Security Center as part of your Windows XP Operating System package. You can only get XP Protection Center from infected websites and corrupt downloads. There’s a world of difference in that alone.
Before you even see the fateful pop up screen, you should get a real antispyware program. It should be complete with removal and prevention. Even better, try looking for a 100% removal guarantee, since not all antispyware programs are the same.